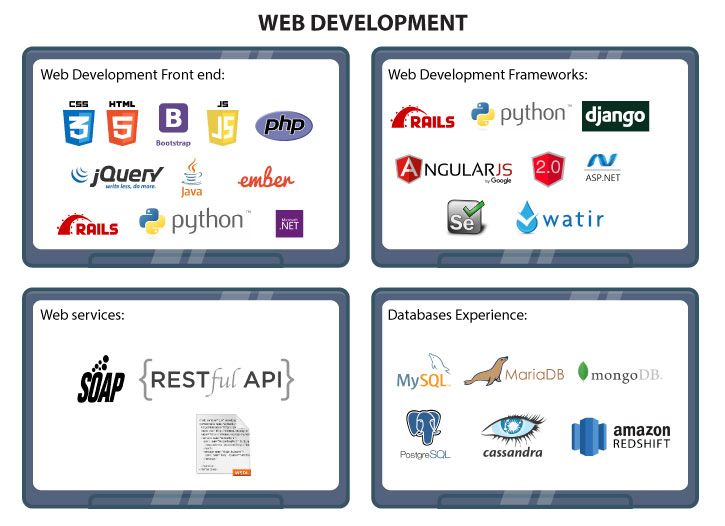
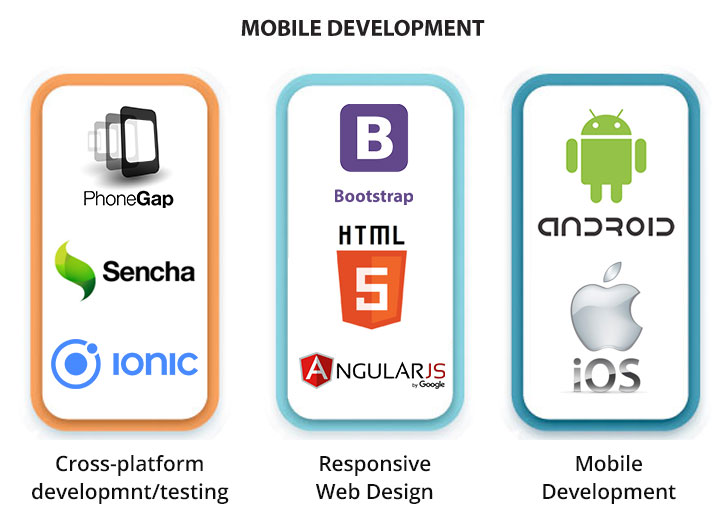
Product R&D Overview
ASM enhances business values of customers by partnering with them in their product R&D and deliver innovative solutions
With decades of experience in the tech industry, we are the preferred technology partner for many global companies.
The ASM Edge
Our customers have found a path-breaking difference in their product development experience right from analysis to delivering a complete solution using cutting-edge technologies, with our proficiency in Open Source and proprietary tools/software.
Our expertise in the Networking, Wireless, Security, Cloud and Virtualization products can help customers in delivering quality solutions to the technology world. We also provide technical support for wide range of products.
Core Competencies






Domain Expertise
Security
Network Security
- Scripts to simulate and validate DDoS and IP Address Spoofing attacks.
- Rule Engine Automation framework to simulate and validate various networking attacks [IP Address Spoofing, Password-Based Attacks, Denial-of-Service Attack, Man-in-the-Middle Attack].
- Network Security: We work with the largest networking companies to qualify their product by simulating threats using various Open Source, proprietary and in-house developed tools.
- Conformance Testing – to acquire the required security related certifications (Example: Common Criteria Certification, OCSP user authentication).
- Handling Exfiltration Domains: Tunnelling domains detection on the fly and block them once it’s been identified.
- Custom List of domains: to define whitelists and blacklists for additional protection
- Secure DNS – DNS Firewall, Advanced DNS Protection, Network Insight, Threat Mitigation
- Network Configuration & Change Management
- IP Address Management
- Threat Insight
- Threat Protection
- Advanced DNS Protection (ADP)
- Virtual Advanced DNS Protection (vADP)
- DNS Cache Acceleration (DCA)
Virtual DNS Cache Acceleration (vDCA) - DNS/DHCP Reporting and Analytics
- DNS Firewall
- Outbound Message broker
- Parental Control Profile (PCP)
- DNS Traffic Controller (DTC)
- Threat Analytics
- Multi-Master DNS Server (MMDNS)
- DNS Response Policy Zone (RPZ)
Cloud Security
The most challenging and overwhelming task in today’s IT needs is to ensure that the data is secure when deployed in the cloud environment. ASM has achieved this by defining security testing methodologies. In-house experts help our clients to measure the effectiveness of security environment by emulating a wide range of threats and attack scenarios.
Our key capabilities include:
- Working with products providing cloud security – on secure cloud [AWS, Rackspace, Azure and Google Cloud] and on-premises servers.
- Container security
- Comprehensive security visibility and continuous compliance for public cloud infrastructure – Cloud Services (Comprehensive visibility of cloud infrastructure), Servers (Security & compliance for virtual machines & host operating systems), Containers (Covering microservices & applications across all container deployments), Integrations (Seamless integration into DevOps process)
- SaaS Application Protection
- Virtualization support for Amazon Web Services (AWS), Microsoft Azure & Google Cloud Platform (GCB)
Cyber Security
Cyber Threats are serious and can bring your productivity and businesses to stand still. It can cause considerable financial and reputational damage to organizations. Today’s targeted attacks pose risk to both data and infrastructure inside an enterprise. Data can be sensitive information that may be intellectual property, financial data, corporate data or other types of data causing negative consequences if exposed by cyber attacks. Some of the common types of attacks seen today are Phishing, Malware, Ransomware, Cross Site Scripting, DoS, DDoS and Man in the Middle attack. In order to secure the business enterprise, it becomes important to detect the cyber attacks, report upon and mitigate the threats at the earliest.
ASM with expertise in Cybersecurity can provide a wide range of offerings supporting dedicated and hybrid architectures across the full security technology stack. Our solution focuses on Identity Access Management and Cyber Security domains.
With rich experience in Cloud Architecture and Datacenter, we can provide services in following areas –
- Internet of Things security
- Security analytics
Mobile Management & Security
Unified endpoint management (Platform, Secure Workspace, Analytics, Tunnel), Threat Defense, OS (Android, iOS, Mac OS, Win10, Linux).
Working with products providing endpoint security and solutions for MDM, MAM, Content Management, BYOD, Workflow Automation.
Endpoint Visibility and Control Platform – managed detection and response (MDR) services
Networking IP Services
Networking
Our key capabilities include:
- Switching, Routing and DDI (Secure DNS, DHCP, RADIUS and IPAM)
- Develop products using networking protocols like MPLS, DNS, DHCP, FTP, TFTP, HTTP, HTTPS etc..
- Qualifying hardware for networking products.
- Create test environments involving third-party solutions such as Cisco ISE, Microsoft Management, Riverbed and F5 Load Balancer. Proficiency in Open Source and proprietary tools/software.
- Building Software Defined Networking (SDN) solutions.
SD-WAN
The software-defined wide-area network (SD-WAN) is a specific application of software-defined networking (SDN) technology applied to WAN connections, which are used to connect enterprise networks – including branch offices and data centers – over large geographic distances.
Software Defined Networking (SD WAN) solutions to cater different segments including retail stores, health care units, logistics hubs, insurance branches, etc.
Deployment and testing of SD WAN solutions across WAN including:
- Validating network traffic
- Managing and monitoring network traffic
- Configure WAN & ACL policies
- Manage Policies to allow/block sites
Wireless
ASM is working with some of the largest WLAN companies. We have in-depth industry experience in developing Cloud-based Wi-Fi solutions, which can scale up to 50,000+ Access Points.
Our key capabilities include:
- Over 150k person-hours of experience in Wireless LAN Technology.
- WLAN domain expertise enables us to drive several Wi-Fi projects from scratch to final product.
- Access Point and Controller Analytics
- IoT gateway – Enhance the Access Points to act as IoT gateway
- Cloud based Access Points – Control the Access points using Cloud Controller deployed in AWS or Azure
- Machine Learning – Predict controllers or Access Points failures using historical data
Cloud Infrastructure
Cloud Services
With a growing trend in innovation and initiatives, business of all sizes are transforming to Cloud services. Undoubtedly, Cloud computing offers numerous benefits to organizations including business agility, collaboration,
pay-as-you-go pricing models, scalability and flexibility.
Our Services include:
- Qualifying cloud-based applications and testing many of the larger cloud-based environments including Amazon’s EC2 environment and Microsoft’s Azure platform, and
- Building data center in a Microsoft Azure environment using the N-tier architecture. This includes identifying tools to create load, traffic and simulate real application usage.
Our key capabilities include:
- Cloud: Qualifying Cloud and Networking based products for various customers using AWS, Microsoft Azure, Google Cloud and OpenStack.
- Automating Cloud and networking products and end-to-end deployment in the Cloud environment.
- Implementation setup of private and hybrid Cloud infrastructure using OpenStack in provisioning, creating re-usable templates and Stack deployments.
- Virtualization: Configuring and deploying various networking products into virtualization servers such as VMware, Hyper-V, Xen, Cisco SREV, Riverbed VSP.
- Amazon Web Services (AWS): Handling ASG, Load Balancer, Amazon S3, Amazon ELB, Amazon EC2, Amazon Route53 and so on.
DevTestSecOps
Framework/Tool Development
The ASM has innovated, improvised and customized standard frameworks to suit business needs. Our automation frameworks are scalable and deployable across multifarious technological products.
- CI/CD Framework: CI/CD framework integrated with Jenkins, Perforce/GitHub and JIRA along with security tools (Qualys, Nessus and Coverity).
- RESTful API: RESTful API framework supports the functional and performance tests on various products.
- Performance Monitor: Tracks performance statistics against various builds and across products.
- API/Selenium Test Framework: In-house developed framework that is used to test UI & API responses.
- Data Parser: This tool helps you parse through large log files and filter events based on keywords, timestamps or tags via the Web UI or via our RESTful API.